Posts (page 37 of 43)
-
Parsing .NET ViewState Jan 27, 2012
The JavaScript-based parser has been moved to a github repository.
Background on parsing unencrypted ViewState is here followed by part two.
.NET ViewState Byte Sequences
Byte(s) Explanation 0x02 […] Unsigned integer, compose value from 7 bits of each following byte until leading 8th bit equals 0. 0x0201 == 00000010 00000001 == 1 0x027f == 00000010 01111111 == 127 0x028101 == 00000010 10000001 00000001 == 1 + (1 « 7) == 129 0x02a1b22a == 00000010 10100001 10110010 00101010 == 33 + (98 « 7) + (42 « 14) == 44052769 0x03 [length] […] Container of [length] Booleans 0x05 [length] […] String, a container of [length] bytes 0x09 RGBA component 0x0B […] 0x00 String, usually NULL-terminated, i.e. read bytes until 0x00. 0x0f Pair (tuple of two objects) 0x10 Triplet (tuple of three objects) 0x15 [length] Array of strings 0x16 [length] Container of objects 0x18 Control state 0x1b [12 bytes] Unit 0x1e [length] […] String (identical to 0x05) 0x1f [number] String reference 0x24 [36 bytes] UUID 0x64 empty node 0x65 empty string 0x66 Number 0 0x67 Boolean true 0x68 Boolean false 0xff01 ViewState preamble Notes The number of elements in a container is defined by [length], which is one or more bytes interpreted as a number in the manner of 0x02. A container may be empty, i.e. [length] is 0x00. -
The Twelve Web Security Truths Nov 16, 2011
My current writing project has taken time away from adding new content lately. Here’s a brief interlude of The Twelve Web Security Truths I’ve been toying with as a side project. They are modeled on The Twelve Networking Truths from RFC 1925.
- Software execution is less secure than software design, but executing code attracts actual users.
- The time saved by not using parameterized queries to build SQL statements should be used to read about using parameterized queries.
- Same Origin Policy restricts the DOM access and JavaScript behavior of content loaded from multiple origins. Malware only cares about plugin and browser versions.
- Content with XSS vulns are affected by the Same Origin Policy, which is nice for XSS attacks that inject into the site’s origin.
- CSRF countermeasures like Origin headers mitigate CSRF, not XSS. Just like X-Frame-Options mitigates clickjacking, not XSS.
- Making data safe for serialization with JSON does not make the data safe for the site.
- There are four HTML injection vulns in your site today. Hackers will find two of them, the security team will find one, the dev team will introduce another one tomorrow.
- Deny lists miss the attack payload that works.
- A site that secures user data still needs to work on the privacy of user data.
- Hashing passwords with 1,000-round PBKDF2 increases the work factor to brute force the login page by a factor of 1. Increasing this to a 10,000-round PBKDF2 scheme provides an additional increase by a factor of 1.
- The vulnerabilities in “web 2.0” sites occur against the same HTML and JavaScript capabilities of “web 1.0” sites. HTML5 makes this different in the same way.
- A site is secure when a compromise can be detected, defined, and fixed with minimal effort and users are notified about it.
- Off-by-one errors only happen in C.
-
RSA Europe 2011 Oct 12, 2011
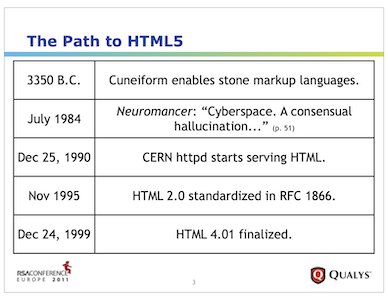
Here are the slides for my presentation at RSA 2011 Europe. The topic was HTML5 with an emphasis on distinguishing between HTML5 features that may present vulns vs. how HTML5 would simply be leveraged as part of older exploits.
It also touches on broader aspects of web security such as design vs. implementation issues, the impact of mobile devices, and how using frameworks can improve security – as long as the frameworks themselves are good.
I iterated on this content later in 2012.